base on Open EDR public repository # OpenEDR
[](https://openedr.com/)
[](https://openedr.com/register/) [](mailto:
[email protected])
[](https://www.youtube.com/watch?v=lfo_fyinvYs "OpenEDR - Getting Started")
We at OpenEDR believe in creating a cybersecurity platform with its source code openly available to the public, where products and services can be provisioned and managed together. EDR is our starting point.
OpenEDR is a full-blown EDR capability. It is one of the most sophisticated, effective EDR code base in the world and with the community’s help, it will become even better.
OpenEDR is free and its source code is open to the public. OpenEDR allows you to analyze what’s happening across your entire environment at the base-security-event level. This granularity enables accurate root-causes analysis needed for faster and more effective remediation. Proven to be the best way to convey this type of information, process hierarchy tracking provides more than just data, they offer actionable knowledge. It collects all the details on endpoints, hashes, and base and advanced events. You get detailed file and device trajectory information and can navigate single events to uncover a larger issue that may be compromising your system.
OpenEDR’s security architecture simplifies *breach detection, protection, and visibility* by working for all threat vectors without requiring any other agent or solution. The agent records all telemetry information locally and then will send the data to locally hosted or cloud-hosted ElasticSearch deployments. Real-time visibility and continuous analysis are vital elements of the entire endpoint security concept. OpenEDR enables you to perform analysis into what's happening across your environment at base event level granularity. This allows accurate root cause analysis leading to better remediation of your compromises. Integrated Security Architecture of OpenEDR delivers Full Attack Vector Visibility including MITRE Framework.
## Quick Start
The community response to OpenEDR has been absolutely amazing! Thank you. We had a lot of requests from people who want to deploy and use OpenEDR easily and quickly. We have a roadmap to achieve all these. However in the meanwhile, we have decided to use the Comodo Dragon Enterprise platform with OpenEDR to achieve that. By simply opening an account, you will be able to use OpenEDR. No custom installation, no log forwarding configuration, or worrying about storing telemetry data. All of that is handled by the Comodo Dragon Platform. This is only a short-term solution until all the easy-to-use packages for OpenEDR is finalized. In the meanwhile do take advantage of this by emailing
[email protected] to get you up and running!
## Components
The Open EDR consists of the following components:
* Runtime components
* Core Library – the basic framework;
* Service – service application;
* Process Monitor – components for per-process monitoring;
* Injected DLL – the library which is injected into different processes and hooks API calls;
* Loader for Injected DLL – the driver component which loads injected DLL into each new process
* Controller for Injected DLL – service component for interaction with Injected DLL;
* System Monitor – the genetic container for different kernel-mode components;
* File-system mini-filter – the kernel component that hooks I/O requests file system;
* Low-level process monitoring component – monitors processes creation/deletion using system callbacks
* Low-level registry monitoring component – monitors registry access using system callbacks
* Self-protection provider – prevents EDR components and configuration from unauthorized changes
* Network monitor – network filter for monitoring the network activity;
* Installer
Generic high-level interaction diagram for runtime components
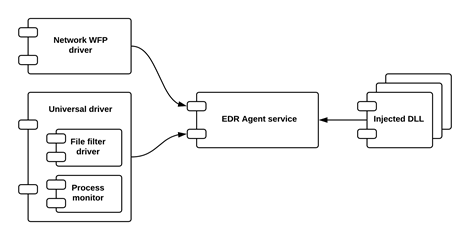
For details, you can refer here: https://techtalk.comodo.com/2020/09/19/open-edr-components/
# Community
* Community Forums: https://community.openedr.com/
* Join Slack [](https://openedr.com/register/)
* Registration [](mailto:
[email protected])
# Roadmap
Please refer here for project roadmap : https://github.com/ComodoSecurity/openedr_roadmap/projects/1
## Getting Started
Please take a look at the following documents.
1. [Getting Started](getting-started/InstallationInstructions.md)
2. [Build Instructions](getting-started/BuildInstructions.md)
3. [Docker Installation](getting-started/DockerInstallation.md)
4. [Setting up Elasticsearch Kibana and Logstash](getting-started/SettingELK.md)
5. [Setting up Openedr and File beat](getting-started/SettingFileBeat.md)
6. [Editing Alerting Policies](getting-started/EditingAlertingPolicies.md)
7. [Setting Up Kibana](getting-started/SettingKibana.md)
# Releases
https://github.com/ComodoSecurity/openedr/releases/tag/release-2.5.1
# Screenshots
How OpenEDR integration with a platform looks like and also a showcase for openedr capabilities
Detection / Alerting
[](https://enterprise.comodo.com/dragon/)
Event Details
[](https://enterprise.comodo.com/dragon/)
Dashboard
[](https://enterprise.comodo.com/dragon/)
Process Timeline
[](https://enterprise.comodo.com/dragon/)
Process Treeview
[](https://enterprise.comodo.com/dragon/)
Event Search
[](https://enterprise.comodo.com/dragon/)
", Assign "at most 3 tags" to the expected json: {"id":"12167","tags":[]} "only from the tags list I provide: [{"id":77,"name":"3d"},{"id":89,"name":"agent"},{"id":17,"name":"ai"},{"id":54,"name":"algorithm"},{"id":24,"name":"api"},{"id":44,"name":"authentication"},{"id":3,"name":"aws"},{"id":27,"name":"backend"},{"id":60,"name":"benchmark"},{"id":72,"name":"best-practices"},{"id":39,"name":"bitcoin"},{"id":37,"name":"blockchain"},{"id":1,"name":"blog"},{"id":45,"name":"bundler"},{"id":58,"name":"cache"},{"id":21,"name":"chat"},{"id":49,"name":"cicd"},{"id":4,"name":"cli"},{"id":64,"name":"cloud-native"},{"id":48,"name":"cms"},{"id":61,"name":"compiler"},{"id":68,"name":"containerization"},{"id":92,"name":"crm"},{"id":34,"name":"data"},{"id":47,"name":"database"},{"id":8,"name":"declarative-gui "},{"id":9,"name":"deploy-tool"},{"id":53,"name":"desktop-app"},{"id":6,"name":"dev-exp-lib"},{"id":59,"name":"dev-tool"},{"id":13,"name":"ecommerce"},{"id":26,"name":"editor"},{"id":66,"name":"emulator"},{"id":62,"name":"filesystem"},{"id":80,"name":"finance"},{"id":15,"name":"firmware"},{"id":73,"name":"for-fun"},{"id":2,"name":"framework"},{"id":11,"name":"frontend"},{"id":22,"name":"game"},{"id":81,"name":"game-engine "},{"id":23,"name":"graphql"},{"id":84,"name":"gui"},{"id":91,"name":"http"},{"id":5,"name":"http-client"},{"id":51,"name":"iac"},{"id":30,"name":"ide"},{"id":78,"name":"iot"},{"id":40,"name":"json"},{"id":83,"name":"julian"},{"id":38,"name":"k8s"},{"id":31,"name":"language"},{"id":10,"name":"learning-resource"},{"id":33,"name":"lib"},{"id":41,"name":"linter"},{"id":28,"name":"lms"},{"id":16,"name":"logging"},{"id":76,"name":"low-code"},{"id":90,"name":"message-queue"},{"id":42,"name":"mobile-app"},{"id":18,"name":"monitoring"},{"id":36,"name":"networking"},{"id":7,"name":"node-version"},{"id":55,"name":"nosql"},{"id":57,"name":"observability"},{"id":46,"name":"orm"},{"id":52,"name":"os"},{"id":14,"name":"parser"},{"id":74,"name":"react"},{"id":82,"name":"real-time"},{"id":56,"name":"robot"},{"id":65,"name":"runtime"},{"id":32,"name":"sdk"},{"id":71,"name":"search"},{"id":63,"name":"secrets"},{"id":25,"name":"security"},{"id":85,"name":"server"},{"id":86,"name":"serverless"},{"id":70,"name":"storage"},{"id":75,"name":"system-design"},{"id":79,"name":"terminal"},{"id":29,"name":"testing"},{"id":12,"name":"ui"},{"id":50,"name":"ux"},{"id":88,"name":"video"},{"id":20,"name":"web-app"},{"id":35,"name":"web-server"},{"id":43,"name":"webassembly"},{"id":69,"name":"workflow"},{"id":87,"name":"yaml"}]" returns me the "expected json"