AI prompts
base on Best practices for segmentation of the corporate network of any company 
# Best-practice-for-network-segmentation
## What is this?
This project was created to publish the best practices for segmentation of the corporate network of any company. In general, the schemes in this project are suitable for any company.
## Where can I find diagrams?
Graphic diagrams are available in the [Release page](https://github.com/sergiomarotco/Best-practice-for-network-segmentation/releases)</br>
The schema sources are located in the [repository](https://github.com/sergiomarotco/Best-practice-for-network-segmentation/tree/main)
## Schematic symbols
Elements used in network diagrams:<br/>
<br/>
Crossing the border of the rectangle means crossing the firewall.
## Level 1 of network segmentation: basic segmentation<br/>

### Advantages
Basic segmentation to protect against basic targeted attacks that make it difficult for an attacker to advance on the network.
Basic isolation of the productive environment from the corporate one.
### Disadvantages
The default corporate network should be considered potentially compromised. Potentially compromised workstations of ordinary workers, as well as workstations of administrators, have basic and administrative access to the production network.
In this regard, the compromise of any workstation can theoretically lead to the exploitation of the following attack vector. An attacker compromises a workstation in the corporate network. Further, the attacker either elevates privileges in the corporate network or immediately attacks the production network with the rights that the attacker had previously obtained.
### Attack vector protection
Installation the maximum number of information protection tools, real time monitoring suspicious events and immediate response.<br/>
OR!<br/>
Segmentation according to level 2 requirements<br/>
## Level 2 of network segmentation: adoption of basic security practices<br/>

### Advantages
More network segments in the corporate network.<br/>
Full duplication of the main supporting infrastructure for production network such as:
1. mail relays;
2. time servers;
3. other services, if available.<br/>
Safer software development. Recommended implementing DevSecOps at least Level 1 of the [DSOMM](https://dsomm.owasp.org/circular-heatmap), what requires the introduction of a separate storage of secrets for passwords, tokens, cryptographic keys, logins, etc., additional servers for SAST, DAST, fuzzing, SCA and another DevSecOps tools.
In case of problems in the supporting infrastructure in the corporate segment, this will not affect the production environment.
It is a little harder for an attacker to compromise a production environment.<br/>
Or you can implement at least Level 2 of the [SLSA](https://slsa.dev).
### Disadvantages
As a result, this leads to the following problems:
1. increasing the cost of ownership and the cost of final services to customers;
2. high complexity of maintenance.
## Level 3 of network segmentation: high adoption of security practices<br/>
The company's management (CEO) understands the role of cybersecurity in the life of the company. Information security risk becomes one of the company's operational risks. Depending on the size of the company, the minimum size of an information security unit is 15-20 employees.

### Advantages
Implementing security services such us:
1. security operation center (SIEM, IRP, SOAR, SGRC);
2. data leak prevention;
3. phishing protection;
4. sandbox;
5. intrusion prevention system;
6. vulnerability scanner;
7. endpoint and ATP protection;
8. web application firewall;
9. backup server.
### Disadvantages
High costs of information security tools and information security specialists.
## Level 4 of network segmentation: advanced deployment of security practices at scale
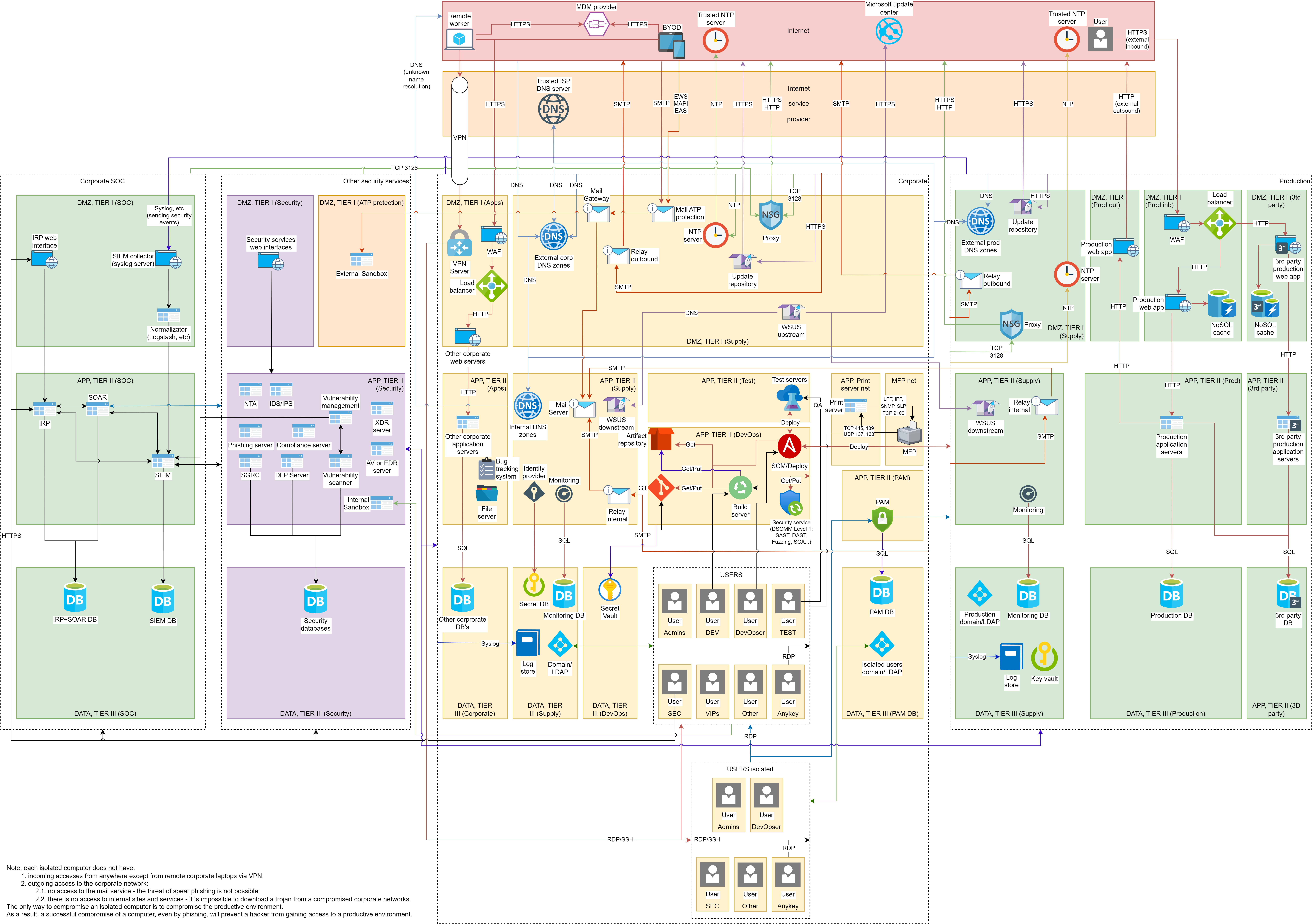
Each production and corporate services has its own networks: Tier I, Tier II, Tier III.
The production environment is accessed from isolated computers. This type of segmentation is called an air gap, this is close to protecting state secrets. Each isolated computer does not have:
1. incoming accesses from anywhere except from remote corporate laptops via VPN;
2. outgoing access to the corporate network:
- no access to the mail service - the threat of spear phishing is not possible;
- there is no access to internal sites and services - it is impossible to download a trojan from a compromised corporate networks.
🔥Only one way to compromise an isolated computer is to compromise the production environment. As a result, a successful compromise of a computer, even by phishing, will prevent a hacker from gaining access to a production environment.
Implement other possible security services, such as:
1. privileged access management;
2. internal phishing training server;
3. compliance server (configuration assessment).
### Advantages
Implementing security services such us:
1. privileged access management;
2. internal phishing training server;
3. compliance server (configuration assessment);
4. strong protection of your production environment from spear phishing.
🔥Now the attacker will not be able to attack the production network, because now a potentially compromised workstation in the corporate network basically does not have network access to the production. Related problems:
1. separate workstations for access to the production network - yes, now you will have 2 computers on your desktop;
2. other LDAP catalog or Domain controller for production network;
3. firewall analyzer, network equipment analyzer;
4. netflow analyzer.

### Disadvantages
Now you will have 2 computers on your desktop if you need access to production network. It hurts 😀
## Support the project
[Please subscribe - this is free support for the project](https://www.instagram.com/lizzibi)
## Have an idea for improvement?
* Submit your pull request;
* Create [issue](https://github.com/sergiomarotco/Best-practice-for-network-segmentation/issues/new);
* Start [discussion](https://github.com/sergiomarotco/Best-practice-for-network-segmentation/discussions).
## If u like it?
[Please subscribe - this is free support for the project](https://www.instagram.com/lizzibi)

", Assign "at most 3 tags" to the expected json: {"id":"5280","tags":[]} "only from the tags list I provide: [{"id":77,"name":"3d"},{"id":89,"name":"agent"},{"id":17,"name":"ai"},{"id":54,"name":"algorithm"},{"id":24,"name":"api"},{"id":44,"name":"authentication"},{"id":3,"name":"aws"},{"id":27,"name":"backend"},{"id":60,"name":"benchmark"},{"id":72,"name":"best-practices"},{"id":39,"name":"bitcoin"},{"id":37,"name":"blockchain"},{"id":1,"name":"blog"},{"id":45,"name":"bundler"},{"id":58,"name":"cache"},{"id":21,"name":"chat"},{"id":49,"name":"cicd"},{"id":4,"name":"cli"},{"id":64,"name":"cloud-native"},{"id":48,"name":"cms"},{"id":61,"name":"compiler"},{"id":68,"name":"containerization"},{"id":92,"name":"crm"},{"id":34,"name":"data"},{"id":47,"name":"database"},{"id":8,"name":"declarative-gui "},{"id":9,"name":"deploy-tool"},{"id":53,"name":"desktop-app"},{"id":6,"name":"dev-exp-lib"},{"id":59,"name":"dev-tool"},{"id":13,"name":"ecommerce"},{"id":26,"name":"editor"},{"id":66,"name":"emulator"},{"id":62,"name":"filesystem"},{"id":80,"name":"finance"},{"id":15,"name":"firmware"},{"id":73,"name":"for-fun"},{"id":2,"name":"framework"},{"id":11,"name":"frontend"},{"id":22,"name":"game"},{"id":81,"name":"game-engine "},{"id":23,"name":"graphql"},{"id":84,"name":"gui"},{"id":91,"name":"http"},{"id":5,"name":"http-client"},{"id":51,"name":"iac"},{"id":30,"name":"ide"},{"id":78,"name":"iot"},{"id":40,"name":"json"},{"id":83,"name":"julian"},{"id":38,"name":"k8s"},{"id":31,"name":"language"},{"id":10,"name":"learning-resource"},{"id":33,"name":"lib"},{"id":41,"name":"linter"},{"id":28,"name":"lms"},{"id":16,"name":"logging"},{"id":76,"name":"low-code"},{"id":90,"name":"message-queue"},{"id":42,"name":"mobile-app"},{"id":18,"name":"monitoring"},{"id":36,"name":"networking"},{"id":7,"name":"node-version"},{"id":55,"name":"nosql"},{"id":57,"name":"observability"},{"id":46,"name":"orm"},{"id":52,"name":"os"},{"id":14,"name":"parser"},{"id":74,"name":"react"},{"id":82,"name":"real-time"},{"id":56,"name":"robot"},{"id":65,"name":"runtime"},{"id":32,"name":"sdk"},{"id":71,"name":"search"},{"id":63,"name":"secrets"},{"id":25,"name":"security"},{"id":85,"name":"server"},{"id":86,"name":"serverless"},{"id":70,"name":"storage"},{"id":75,"name":"system-design"},{"id":79,"name":"terminal"},{"id":29,"name":"testing"},{"id":12,"name":"ui"},{"id":50,"name":"ux"},{"id":88,"name":"video"},{"id":20,"name":"web-app"},{"id":35,"name":"web-server"},{"id":43,"name":"webassembly"},{"id":69,"name":"workflow"},{"id":87,"name":"yaml"}]" returns me the "expected json"